What is the value of an informed decision? At OODA Loop, we seek to surface decision intelligence that provides meaningful perspective for leaders and analysts looking to make the most informed decisions possible. This list below represent developments that fit the category of operating in a VUCA world, identifying and responding to Gray Rhino risks, or opportunities from advancements in emerging technology domains. These are issues we think our members should be tracking and map to collection requirements for our team to keep you as informed as possible. This report is updated throughout the year with the goal of providing a quick reference for corporate boards and their directors in need of strategic insights. CEOs and other C-Suite leaders can use this list to update and shape strategies and actions. This report is best read in conjunction with the yearly OODA Almanac, which characterizes key trends which will drive actions throughout the year.
Already a subscriber? Sign In.
Want our most exclusive content? Subscribers receive:
- Exclusive Content Access: Research and expert driven analysis to inform your decision-making. Over ten thousand articles on disruptive technologies, cybersecurity, geo-political risk, and national security technology issues available only to subscribers. Our Daily Global Pulse will let you know what premium content has been recently published as well as hand-curate the top stories of the day with executive level summaries.
- The OODA Network Dispatch: Our weekly newsletter keeps you apprised of emerging trends and upcoming events so you can stay informed and aware of issues that could impact you or your organization.
- Community Engagement: Engage in our dynamic Slack Workspace which serves as a hub for professionals and experts to exchange ideas, strategies, insights, and opportunities.
- Premium Content
- Slack Community
- Weekly Newsletter
- OODAcon Invite
- All subscriber Benefits
- Monthly Meetings
- In-person Network Events
- Network Slack Channels
- 50% OODAcon Discount
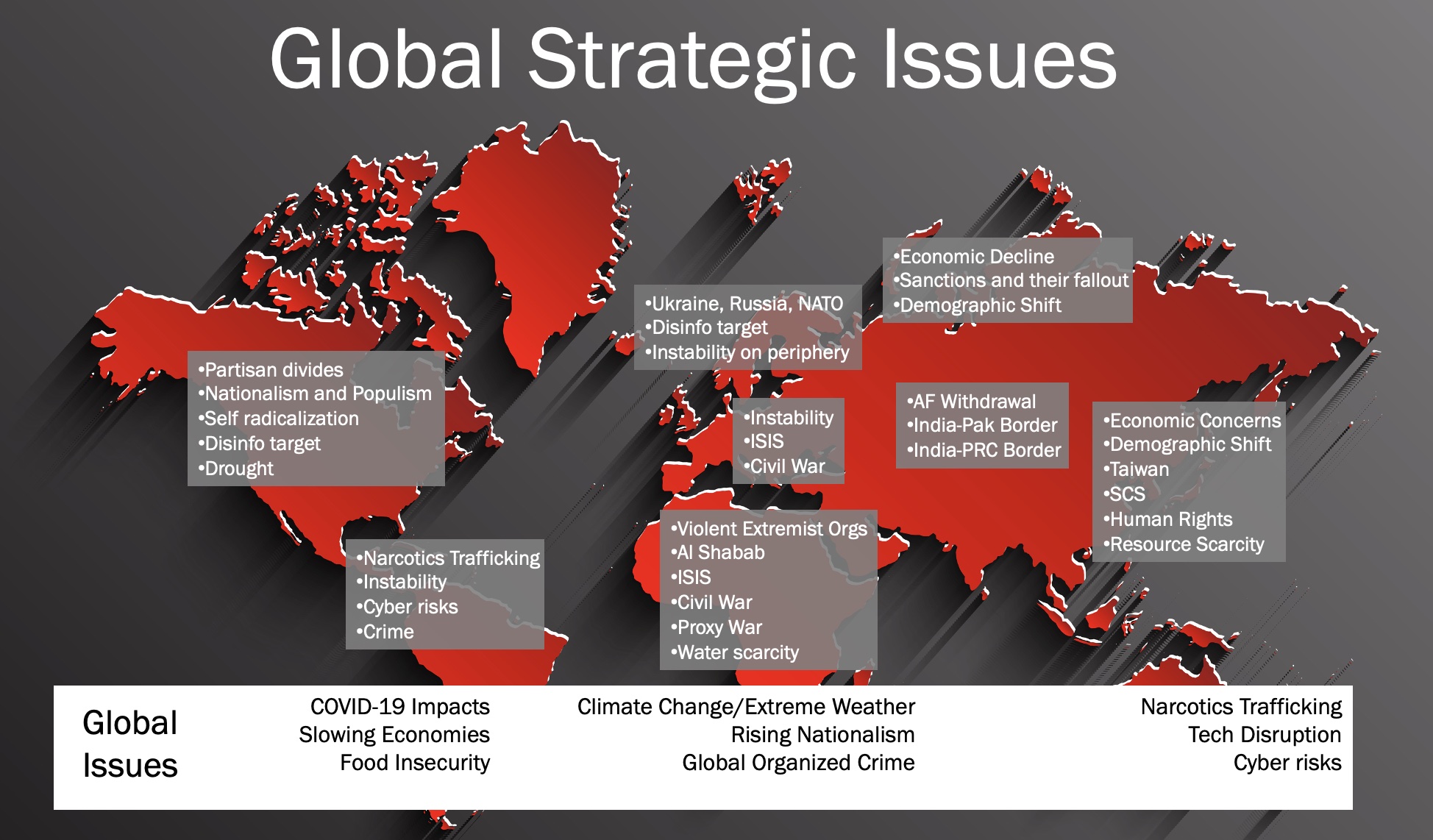
We categorize and summarize these big trends into Geopolitical Issues, Technology Trends, Cyber Risk Issues, and Recommendations for Action.
Overall Assessment:
- Global economy shifting to favor more open societies
Geopolitical Issues
- What great power competition means for your business
- The Russian invasion of Ukraine and impact in Europe and Globally
- Bleak economic prospects for China and impact on business environment
- Networked Extremism and the Convergence of Crime, Insurgency, Corruption
- Food Security as an increasing driver of geopolitics
- The Demographic Time Bomb
Technology Trends
- New risks and opportunities in the age of converged technologies
- Automation, new sensors and new communications
- Uncertainties in computer chip supply chains
- The need to optimize small data, reduce cost of training ML, and improve NLP
- The coming metaverse and its potential to disrupt the Internet
- Unstoppable Bitcoin
Cyber Risks
- Cyber and Geopolitical Risks
- The Rise of Ransomware
Recommendations for Action
- What businesses should do about continuous cyber risks
- Using scenario planning to reduce risk, seek opportunities and inform business strategies
- Updating your strategy for the US drought and food security
- Reshoring Accelerating
Overall Assessment
The Global Economy Is In Transition: Expect continued disruptions and hard times for many, but shift to US and open societies is apparent
The global economy is slowed in 2022 and early 2023. We advised business and government decision makers to expect a full recession that will impact the market of most products and services. It is still prudent to be ready for this size of shock. However, there are significant signs of strength including in the US unemployment numbers, US equity markets, and what seems to be a tapering off of US inflation. Globally there are many other pressures and most all nations are doing worse than the US, but in general the open societies are doing better. With the awakening to the horrors of war in Europe and the realization that the CCP and other authoritarian regimes are slow to change many open societies are shifting their relationships and supply/trading partners. Amateur pundits are throwing out extreme views on topics like the dollar and its status as the world’s settlement currency. Calmer heads seek to characterize the situation without giving in to histrionics. This is a dynamic time, but risks can be mitigated.
Shocks positive and negative are reviewed below. We also present more action oriented advice for members in this report titled “The US Economy and Entrepreneurship From A Technologist Perspective“
Geopolitical Trends
The Great Nations Are Competing, What Does This Mean For Your Business?
The rise of great power competition and related changes in the international scene are causing changes to corporate risk and opportunities. Businesses have already had to adopt to new sanction regimes, new supply chain disruptions and new hostilities in cyberspace. Expect far more of this type of disruption. Also expect new opportunities, including the opportunity to serve the national security needs of open societies like the US, EU, Japan, ROK, India and many parts of South East Asia.
Modern great power competition is not only on topics like land and geopolitical disputes. Food, water, raw materials like rare-earth elements and technology are front and center in this competition. One critical risk that needs to be understood and mitigated because of this return to great power competition is what it may mean for the global computer chip shortage (we examine scenarios for global computer chip supply chain disruption in this Stratigame). Should tensions rise more between the PRC and Taiwan this could cause the shortage to become a real crisis.
There are many other impacts that flow from great power competition. One is being described by many watchers as the “end of globalization.” Our assessment of trends does not lead us to conclude that globalization is over, but there will certainly be more reshoring of supply chains and more regionalization of trade. Many other impacts are reviewed below.
To inform your strategy with the latest see: Global Risk and Geopolitical Sensemaking
The Russian Invasion of Ukraine and Impact in Europe and globally.
The Russian aggression against Ukraine will have enduring impacts far beyond the region. All companies and all government organizations (including those at local and state levels) should evaluate the potential impact of these hostilities on operations. We are a nation interconnected with the world by complex supply chains and a global high speed internet and must be ready to deal with impacts.
There are many aspects of this to consider. For examine, the fact that many sanctions on Russia were initiated by corporations means Russia may consider these corporations as legitimate targets for attack, including cyber attack and attack against ownership of property inside Russia. Physical attack is thought less likely but should also be assessed as a potential now.
Meanwhile this war has opened the eyes of many in the free world to other threats including the threat from China. This is will very likely lead to more support for collective security alliances like NATO and also to higher levels of investment in defense for many free nations. The traditional (since the end of WWII) stance of Japan to have only a self defense force may soon end, and its shunning of nuclear weapons may also be up for question, something that was unthinkable just months ago. Japan has already dramatically increased its defense budget because of this.
Short term this war has spooked investors, caused massive sanctions against Russia that also impacted western businesses, interrupted supply of food from Ukraine to Europe and Africa, is slowing all Russian oil production (which may one day almost totally cease due to lack of western tech support) and caused increases in government spending at a time when deficits are already out of control.
The invasion is also causing some cracks in Russia’s relationship with Kazakhstan, which has for the most part been in Russia’s orbit until recently. Russia is now blocking the transport of Kazakhstan oil and gas to Europe, which Kazakhstan did not want to happen. Recall that Russia helped put down revolt in Kazakhstan in January just before the invasion. China’s relationship with Russia is changing because of the war. Xi’s visit to Russia in March 2023 resulted in many photo ops and pleasantries, but the outcomes make it pretty clear that China has no intention of backing Russia up and will likely continue to abuse the relationship with Russia. Russia has now agreed to settle many transactions with China in the Yuan.
For additional resources see:
Global Risk and Geopolitical Sensemaking.
Thinking Strategically About What Comes Next and How To Mitigate Risk
We continue to advise business leaders to think of the unthinkable. We have published what this can mean for cybersecurity here: C-Suite Guide: Improving Cybersecurity Posture Before Russia Invades Ukraine. But consider what it means for employees and suppliers who may operate in future war zones, and consider the impact on markets that may temporarily (we hope) shut down due to hostilities.
Signs of Economic Weakness in China Indicates Coming Crisis
The increasingly bleak economic prospects in China are not a surprise to China watchers. And shifting demographics will make things even worse with fewer workers and consumers to support an aging populace. On 16 August 2022, Premier Li Keqiang chaired a State Council executive meeting where the bleak economy is top of the agenda. Li considers new risks the catastrophic flooding in Henan, resurgent Covid-19, inflation of raw material prices and new geopolitical risks. In 2023 these worries continue and indications are that the economy is once again the number one threat to the CCP.
The Yuan is a continually manipulated currency, but even with that it has been weakening against the dollar (by March 2023 it was trading at 6.8 per dollar). There is little transparency into the true financial numbers on the economy in China, but official forecasts are that the GDP growth will slow from 5.2 percent to 4.3 percent. Actual numbers must be much worse. In March 2023 estimates are that China’s industrial firms shrank 22.9% in the first two months this year from a year ago, as the factory sector struggles to claw its way out of the slump caused by COVID-related disruptions. That followed a 4% drop in industrial profits for 2022 and suggests an uneven path to recovery for the economy. Retail sales for January-February showed stronger growth momentum.
By June 2022 the World Bank, JP Morgan, UBS and more began issuing more dire forecasts for GDP in China. Estimates vary, as mentioned above it is hard to get actual numbers to build assessments on , but growth is probably around 3%, much lower than the 5.5% the PRC is claiming.
Many self imposed economic problems are being caused by China taking trade action against companies and countries that criticize the persecution of Uighurs. One salient example is China’s punitive measures against Australian coal imports which is contributing to rolling power outages. Solutions directed to be put in place seem like band-aids. For example, guidance has been given for increasing domestic production and supervising commodities to curb inflation. If only it was that easy! Employment assistance is being ramped up as well, with calls for promotion of labor-intensive industries.
Other issues are being caused by China’s strategy of locking down entire cities and regions to try to fight covid. This lockdown strategy is also fueling internal unrest which is being captured on social media and shared internally even in a nation where surveillance and social scores are in place to mitigate criticism. We are tracking this closely and will continue reporting on this via our daily pulse and research reports.
China’s economic weakness may in part explain their distancing from support to Russia’s invasion of Ukraine. China is still parroting some Russian propaganda on the war, but has been backing away from that a bit and has also been publicly stating they will not supply Russia with weapons or other material for the conflict. This is definitely one to watch.
The reporting in OODA’s News Briefs frequently captures indications of economic weakness. Some factors of note:
- China’s population bomb is coming sooner vice later. China has the fastest aging population in the world and is clearly not ready for the impact this will have
- China remains terribly polluted, which contributes to significant health and quality of life impacts
- China remains heavily dependent on imports of oil, gas, most raw materials and food
- In many areas of the country the nation has been overbuilt, which huge debt being taken on to maintain the pace of this overbuilding for no purpose.
- More foreign investors are deciding not to invest in China because of their true nature being revealed plus impact to supply chains of lockdowns
The extensive dependencies of the entire world on China means economic weakness could pose significant concern. Some of the worse case scenarios could involve an almost total shutdown of industrial production, which would force a devastating restructuring of the global economy and lead to unpredictable outcomes. Since worst case scenarios can certainly come true, we recommend business and government leaders begin asking focused questions on what a PRC economic crisis might mean for supply chains. Some questions to consider:
- What dependencies to pharmaceutical companies have on China? How might drug supplies be interrupted? What plans can be put in place to mitigate those risks?
- What supply chain dependencies relying on the PRC can be shifted to other more open nations?
- How will US goods and services (approx $150B per year) exported to China be impacted by PRC economic slowdown? Can any new markets can be found for US goods and services?
- What would the impact of a PRC economic slowdown be on US GDP? US unemployment?
- What would impact of PRC slowdown be on the US high tech industry? Other industries? Stock markets overall?
- What long term effects might PRC economic slowdown have on US manufacturing and re-shoring?
- What would further economic crisis in PRC mean for the cyber threat environment in the free world? (Consider the scenario where millions of desperate computer savvy individuals will do anything online to survive).
There are obvious questions we are watching regarding how the war in Ukraine will impact China and their potential operations against Taiwan. We are watching this closely.
Networked Extremism and the Convergence of Crime, Insurgency, Corruption.
The evolution of the Internet has provided extremists from multiple geographies with new ways to privately interact to share tactics, plans and coordinate intentions. This networked extremism is a growing threat. It is closely related to the rise in self radicalization seen across western democracies.
These same technologies are enabling new business models of crime. And agile criminals are quicker than ever to exploit current geopolitical events to further their objectives, which is helping to drive a convergence of crime and corruption. The trend towards distributed computing and distributed finance that is providing so many features and benefits to good people is also providing new benefits to bad people and this is also complicating the situation.
In the age of Covid, corruption in the developing world has grown. Corruption in kleptocracies remains a baseline part of governance. And as long as corruption is such a driver in both kleptocracies and so many other countries it will be a major force impeding human progress and disrupting business potential.
Food Security and Inflation are Increasingly Drivers of Geopolitical Action
Food security is becoming a critical factor in geopolitics. The US seems better positioned than most as a net exporter of food, but with enduring drought in the midwest there are concerns and risks that need to be mitigated. Riots in Sri Lanka which have resulted in the resignation of the prime minister is one early example of what the impact of poor food security can bring.
Inflation is also directly related to food security. If people cannot afford to buy food they do not have individual food security. A salient example is the situation in Argentina, where inflation is currently running at an annual rate of 70%. This runaway inflation is causing massive protests. It is not hard to see this type of stress on other nations, including Turkey, which has an annual inflation rate nearing 80%. India could be another. Officially India’s inflation rate is 7% but it has a high debt and is totally dependent on others for imports of oil and other commodities.
Riots are being seen in many other regions. In Kenya the rallying cry at current protests is “no food, no elections!” and people are marching with bowls they expect to be filled.
Looking at the trends in geopolitical tensions, cost of oil/gas (used in fertilizer production) and conflict in Ukraine, it is pretty clear that a global food crisis is gong to hit every continent. In North America we will have it better than others. Here we will complain about not getting out of season fruits or not having our usual variety. But in most other regions it will be a very real fight to avoid mass starvation and widespread malnutrition. Unfortunately, famine is coming for many (Russia and China are both trying to shape blame on this famine to be on the US).
It is puzzling and counter intuitive that in this age of increasing food security issues and inflation there is so little being done to improve the situation. Many actions by leaders are actually counter productive, like shutting down nuclear power plants vice building more, or forcing farmers to reduce nitrogen use to try to reduce atmospheric carbon (cause of dutch protests). There are other methods of reducing nitrogen use besides just dictating reduction, including innovative new technologies for capturing nitrogen for agriculture.
Demographic Time Bomb Having An Impact
The demographic time-bomb impacting industrialized nations has been tracked for decades and now is suddenly impacting global economies. The demographics of most industrialized nations have shifted so there are fewer working age people and more retirement age people. Japan is one of the first major industrialized nations to start to see the impact of graying, but this is a problem for all nations. It is a significant concern for China which has the fastest aging society in history.
Technology Trends
A Convergence Of Technologies Is Creating New Risks and New Opportunities and a Refactoring of Work
The rapidly advancing pace of technology is reflected in the dramatically changing capabilities available in the marketplace today. This is changing the competitive landscape, changing the potential capabilities of your internal architecture, and changing the expectations of your potential clients/customers. In this age of dramatic advancements all should ensure appropriate measures are being put in place to understanding these potential market disruptions and changes to the competitive landscape. The best way to model out potential future disruptions is to examine drivers of tech, which should include assessments of future user/customer demands. For more see: Advanced Technology Sensemaking
When planning the impact of technology on your business or office workflows, it is important to take a look at the convergence of multiple technologies towards mission impact. Do this by maintaining at least a conversational knowledge of every major tech domain and an ability to contemplate how these domains will interact in the near future.
The Many Fields Of Artificial Intelligence Are Building Off Of Each Other
The excitement over ChatGPT and Large Language Models has given way to concern that humanity is rushing too fast into an AI enabled world. The Future of Life Institute published a letter signed by 1000’s of AI experts calling for a new debate over governance of AI and a pause of certain developments while AI is being built. The OODA network has examined what can go wrong with AI and have a series of references here. There are clearly concerns with the negative impacts of AI, but also clear benefits which are often not articulated by those who call out the risks. Our view is both opportunities and risks should be considered, with appropriate governance being put in place to mitigate the risks.
Automation, New Sensors and New Communications Providing Positive Benefits Already
Although still early in the S-Curve, the growing capabilities of automation, including those provided by Artificial Intelligence, Robotics and Robotic Process Automation, are providing positive business benefits and shifting how organizations operate. These efficiencies are needed now more than ever and this will likely accelerate their growth.
New sensors, including new sensors leveraging quantum effects, are changing healthcare and the national security sector and will soon become more widespread and impact wider swaths of the economy.
The benefits of advanced WiFi and Cellular communications and space based communications will improve the ability of organizations to disperse and further support distributed workforces. WiFI and Cellular advancements in particular are also enabling direct device to device communications in ways that will help optimize deployed robotics and advanced manufacturing.
The applications and compute foundation which has enabled knowledge workers to work from anywhere is now an important component of the nation’s infrastructure with impacts discussed further below.
Uncertain Computer Chip Supply Chains Could Impact Multiple Industries
This topic is directly linked to geopolitics and is reviewed above in the context of great power competition. But is should also be viewed from the lens of the technology and changes we should put in place to minimize disruption. The computer chip shortages of 2021 have caused disruptions to parts of the tech sector and several automotive brands, but overall the impact has not been hard on consumers or militaries. This could change if there is a crisis that causes more issues in supply. This is a topic of growing importance to wargame out and will be the topic of additional reporting at OODAloop in the coming months (we examine scenarios for global computer chip supply chain disruption in this Stratigame).
Leveraging new NLP approaches
For over a decade enterprises have focused on ways to optimize the use of large data sets using new algorithms and storage and processing capabilities. This Big Data movement remains important. But there are indications that not enough attention has been placed on the need to analyze smaller data sets where traditional machine learning capabilities are not optimized. The need to analyze small data, accurately, may be of growing importance if the chip shortages discussed above cause even larger disruptions.
Whether data is small or large, most all high end AI/ML capabilities need to be trained. The cost to do this training is rapidly declining, with ARK finance showing data that indicates the cost to train ML models is declining at twice the rate of Moore’s law. This is a good spot to be in for those seeking to use AI to disrupt and continue to improve business models.
Other key breakthroughs include the use of unsupervised learning in new methods of natural language processing. Savvy tech strategists may find this to be the most disruptive of all tech developments. For more see: What Leaders Need to Know About the State of Natural Language Processing
The Metaverse Is Coming And It Will Disrupt The Current Internet
The age of the Metaverse is upon us. The Metaverse is the successor to the Internet of today. It is a future state that will include persistent interoperable virtual worlds and the platforms required to support and interact with them. It will have its own thriving economy and deliver experiences unavailable in the physical world. It will be a primary means of educating our youth and delivering knowledge through life, and will be a leading form of social interaction and entertainment. For more see: What To Know And Do About The Coming Metaverse
Unstoppable Bitcoin
At this point we cannot think of a force that will stop Bitcoin. In years past this was a concern, although the math is solid and it was designed to be distributed, if enough nation’s were allied against it or if laws were changed the system could be destroyed. But doing that would take will and based on the popularity in open societies that will is not there. Too many people, businesses, institutions and communities now believe in Bitcoin. To some degree this is also true of Ethereum and a handful of other approaches to cryptocurrency. To prove this point, consider the shift in attitudes by Secretary of Treasury Janet Yellen, who has now been pulled into the bitcoin fan camp. For more on the disruptive potential of Bitcoin and Ethereum see: What CEOs Need To Know About Bitcoin: Including potential new business models to consider. FYI, we believe the reason the Metaverse is going to be real is the rise of an Ethereum based capability that can be a store of value that works across all stand alone metaverses to build a single interoperable trust layer.
Ethereum is a platform that can be built upon and is the top layer of many other blockchains (the terminology here is L1 and L2 for Level one and Level two). Ethereum upgrades have made it cheap for L2’s to write their results to the Ethereum L1. So L2 developers can build out even more capabilities and use the Ethereum network for security and censorship resistant infrastructure to capture their info. The result is an ecosystem of blockchains with Ethereum at the top. We expect to see a rush to build L2s on Ethereum. This is forming an inescapable center of gravity in the cryptocurrency space. Everyone is building here because everyone is building here. Ethereum may become the de facto global settlement layer for all digital value.
Could it be that Ethereum is becoming for the financial system what TCP/IP is for the Internet?
A Revolution in Materials Science is underway
Recent reports of a breakthrough in room-temperature ambient pressure superconductors (RTAPS) have rightfully stirred excitement. Yet it’s just one piece of the vast innovation puzzle that materials science is solving. Here are five other breakthroughs that are on track to make significant impacts on our lives within the coming decade:
Reprocessable Materials: Sustainability will take on a new meaning as reprocessable plastics, resins, and polymers reshape not only the automotive and healthcare sectors but also consumer goods manufacturing.
Energy Storage Innovations: From solid-state batteries to advanced supercapacitors, energy storage advances promise to boost efficiency in homes, electric vehicles, and even grid systems.
Smart Textiles: With the emergence of health-monitoring clothes and self-healing fabrics, industries from healthcare to fashion and sports will experience a paradigm shift.
3D Printing Materials: High-performance thermoplastics and metal alloys for 3D printing are set to disrupt manufacturing in aerospace, medical technology, and even the construction sector.
Perovskites: This material’s versatility extends to sectors such as solar power, LED technology, lasers, and quantum computing, creating a ripple effect of innovation.
Cyber Risk Trends
Corporate Board and Their Directors Charged With Mitigating Systemic Risks Due To Cyber
A convergence of market forces, new SEC regulations, a new white house strategy and pending legislation make it clear, corporate boards and their directors will be held responsible for cyber risks in their organizations. For more see:
What Corporate Directors Need To Know About Coming SEC Cybersecurity Rules
The Digital Directors Network: Helping corporate boards mitigate systemic risk
Every Director of Every Corporate Board Should Read What Larry Fink Writes
How to Manage Cyber Risk as a Board Director
Stronger Connection Between Geopolitical and Cyber Risks
Over the last two decades as every region of the world and every corner of humanity has increased Internet access, regional issues have increasingly impacted events in cyberspace. This has evolved to the point where every major issue is a cyber issue and cyber risks must be considered as top tier risks for corporate and government leaders. We report on cyber issues on a daily basis and every single day we see this connection between geopolitical risks and cyber risks strengthen.
Ransomware Evolving Fast
The technology of ransomware has evolved in sophistication and the business models of the criminal groups behind it have as well. The result: The threat from ransomware has reached pandemic proportions. Fortunately there are things that can be done to mitigate this threat. For more see: An update on the nature of the ransomware threat
Uncertainty Around Cyber “Net Assessment” Growing
Over the last several decades both government and business leaders have sought ways to measure and comprehend both cyber risk and cyber security. Today there are many metrics in these domains, but few are really actionable in assessing the true state of security. In the end it seems that the only assessment that can be made is wether a given system can be broken, there can never be an assessment that a system cannot be broken. But assessments can be made that inform and prioritize actions to reduce risk.
There is a need for understanding of the cyber dynamic beyond just building action plans to mitigate risk. Companies, governments and citizens need an ability to understand the state of cybersecurity in context of cyber threats. This type of net assessment has always been hard and, due to the now ubiquitous nature of modern technology, is getting harder to make with confidence.
Strategic Actions
The fact that so many sudden changes are happening at the same time complicates situational awareness and can impede optimal decision making, which leads to our most important recommendation. Every organization should assess the current approaches to collecting the right information, assessing it and making informed decisions. For more insights into this see our series on Decision Intelligence.
Mitigate Cyber Risks Through Continuous, Informed Action
A trend we have previously articulated for OODA members is the rapid increase in events that are described in terms of being the most significant in history. Clearly criminals and nations in cyberspace are unrelenting. But leaders should be aware that there are things that can be done to make it harder on adversaries. Mitigating cyber risks takes awareness and action not just from the IT department and CISO but the entire leadership team. The government has a role to play too, but we never advise waiting for the results of any government action (for decades the government has had an “on again, off again” approach to working with industry to help reduce risks). For more, including actionable advice from practitioners on how to mitigate risks, see: Cybersecurity Sensemaking
The FBI and CISA have issued multiple warnings about cyber threats. This underscores that security and its leaders have to be always on. Coverage over weekends and holidays is critical. Build your teams for long term endurance. Burnout can be an issue for many so make it a conscious choice to build in rest and recovery time for your people. For more see: What Corporate Directors Need To Know About Coming SEC Cybersecurity Rules and How to Manage Cyber Risk as a Board Director
In An Age of Uncertainty, Corporate Intelligence and Scenario Planning Is Of Increasing Importance
Businesses now face more than traditional competitive challenges. In the age of continuous crisis there are exogenous threats that must be avoided or mitigated, including many that are just too hard to even try to predict. Tracking risks closely underscores the need for Scenario Planning to inform corporate decision-making. Scenario planning is needed now more than ever. Scenario planning is a methodology for helping leaders think through alternative futures in a way that enables identification of issues. It raises potential outcomes and impacts and helps conceptualize potential risks and opportunities so organizations can be better prepared. We strongly encourage every company, large or small, to set aside dedicated time to focus on ways to improve your ability to understand the nature of the significantly changed risk environment we are all operating in today, and then assess how your organizational thinking should change. For more see: Corporate Sensemaking: Establishing an Intelligent Enterprise
Scenarios should be informed with fact based assessments and observations on strengths and weaknesses of the economy. In the US, the economy will be in a period of turmoil and recession, but may bounce back quicker and in a better position than most others. The US has many advantages including geography, natural resources, agriculture and a system supporting innovation. Recommend that during the coming turmoil businesses should plan for scenarios that include a recovery to a system that is more resilient, more productive and more sustainable than ever before.
All Businesses Need To Plan For Continuous Pandemic/Health Disruption
Covid-19 continues to impact geopolitical relations, with the now released assessment from the US Intelligence Community implying that most scenarios for the rise of Covid-19 put some sort of blame on China. There is not agreement on exactly what happened, but the full report indicates at a minimum China should have done more to alert the world, and it may well have been the fault of poor virus handing at the Wuhan Lab. (read more here).
Tracking the rise or decline in COVID cases is important, but for planning purposes we recommend all businesses and governments plan for COVID always being with us in some way or another.
But the big point here is the same factors that caused Covid to become a pandemic are still present today. We are all still globally connected and sources for virus strain evolution still exist.
Businesses should plan to operate in a world where Covid or Covid-like disruptions will always be with us. What does this mean for the future of your workforce? It is prudent to expect that there will always be a large component of the workforce remote and distributed, but also expect driven achievers to seek to work in person. There is nothing like being in the room when the big decisions are being made.
The Trend To Reshoring Will Only Accelerate: But reshoring requires prudent planning
The trend towards reshoring, nearshoring and friendshoring of existing manufacturing signals a shift for new manufacturing, not just in the US but globally. The fact that no region wants exposed supply chains means all regions will move to having local manufacturing. All regions will need to make their own products, grow their own food, produce their own energy, defend their democracy either alone or with well established alliances, and automate to support aging populations. Reshoring takes time and planning and is never simple. Many famous examples of failed reshoring exist, with many failures due to underestimating complexity. Extensive analysis needs to be done and this takes time for engineering, design, production, finance, procurement.
(last updated 27 March 2024)
Related Reading:
Explore OODA Research and Analysis
Use OODA Loop to improve your decision making in any competitive endeavor. Explore OODA Loop
Decision Intelligence
The greatest determinant of your success will be the quality of your decisions. We examine frameworks for understanding and reducing risk while enabling opportunities. Topics include Black Swans, Gray Rhinos, Foresight, Strategy, Stratigames, Business Intelligence and Intelligent Enterprises. Leadership in the modern age is also a key topic in this domain. Explore Decision Intelligence
Disruptive/Exponential Technology
We track the rapidly changing world of technology with a focus on what leaders need to know to improve decision-making. The future of tech is being created now and we provide insights that enable optimized action based on the future of tech. We provide deep insights into Artificial Intelligence, Machine Learning, Cloud Computing, Quantum Computing, Security Technology, Space Technology. Explore Disruptive/Exponential Tech
Security and Resiliency
Security and resiliency topics include geopolitical and cyber risk, cyber conflict, cyber diplomacy, cybersecurity, nation state conflict, non-nation state conflict, global health, international crime, supply chain and terrorism. Explore Security and Resiliency
